
In today’s digital age, the exchange of personal data has become a lucrative industry. Countless entities gather, sell, and utilize private details about individuals, often without their consent. While this might seem harmless, the implications are far-reaching. Every click, every search, and every purchase adds to the mosaic of our identity. What happens when that mosaic is mishandled?
With technology evolving rapidly, the potential for abuse rises dramatically. Information can easily be misappropriated, leading to devastating outcomes. Fraud, identity theft, and even harassment have emerged as common threats in this landscape. One moment, your details are safely stored; the next, they are in the hands of malicious actors.
Consequently, understanding the dynamics of this ecosystem is crucial. The mechanisms behind data collection often remain hidden from public view, shrouded in a veil of complexity. This obscurity can create a false sense of security, lulling individuals into complacency. Remember, knowledge is power. Being aware of who holds your details is the first step toward safeguarding your privacy.
As the risk of exposure continues to surge, the need for vigilance cannot be overstated. It’s essential to stay informed, take control, and implement protective measures. Ultimately, the more you know about the management of your own identity, the more effectively you can defend against potential threats.
Understanding Data Brokers

In today’s digital landscape, vast amounts of personal details are collected and shared. This information can be utilized for various purposes, some of which can be quite alarming. Understanding how these entities operate helps reveal the complexities involved in the digital marketplace.
These companies are experts at gathering, analyzing, and selling information. They operate quietly in the background, compiling details from multiple sources. This can include social media profiles, public records, and online transactions. Often, individuals have no idea how extensively their personal attributes are tracked and cataloged.
Their operations have significant implications for privacy and security. As they gather extensive profiles, this information becomes a valuable commodity. It can be sold to other organizations, from marketers to those with less noble intentions. Understanding the intricacies of their operations is essential for recognizing potential risks.
- Collection: Information is gathered from various sources.
- Analysis: Entities sort and categorize the data they collect.
- Distribution: Insights are sold to interested parties.
It’s important to recognize that the information gathered is not always benign. There are serious concerns regarding how it can be used maliciously. When these details end up in the hands of those with harmful intentions, the consequences can be severe. Identity theft, targeted scams, and even harassment are just a few examples of the potential fallout.
Understanding how these organizations function empowers individuals to take control of their online privacy. By being informed, people can make better decisions regarding their digital footprints. One must consider the balance between convenience and security in an increasingly connected world.
The Role of Data in Cybercrime
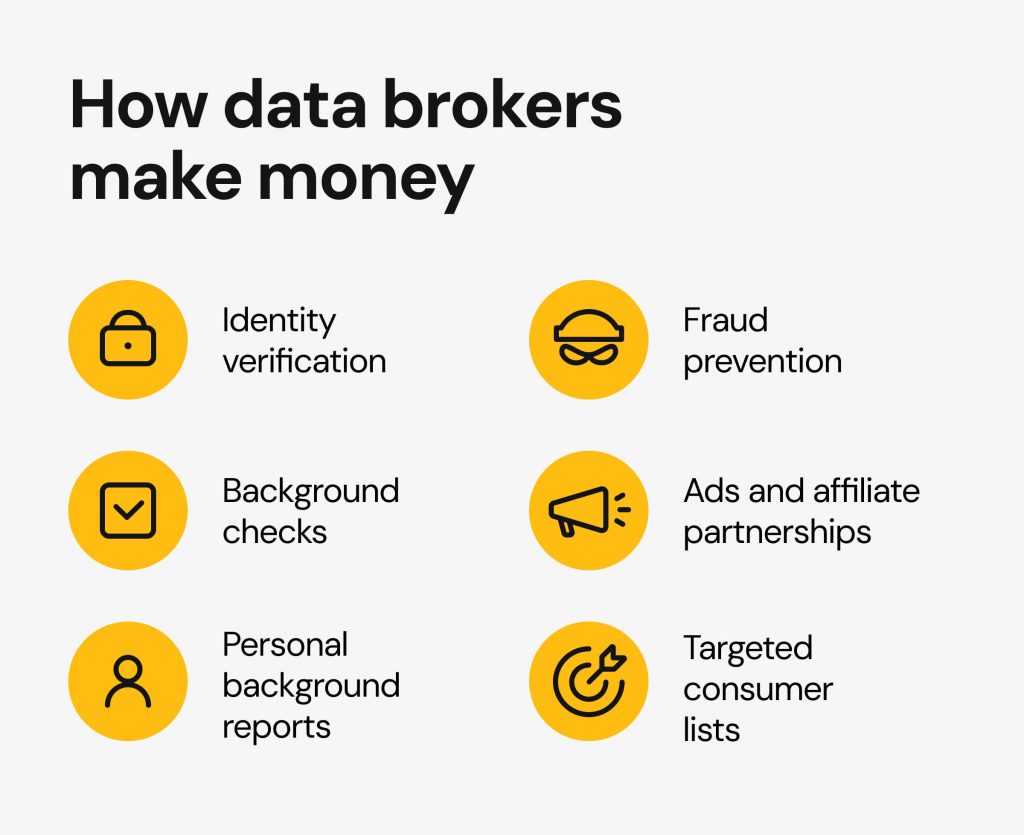
In today’s digital landscape, the availability of personal details has led to new challenges. Many individuals are unaware of how their private information is exploited. It’s a complex web where sensitive data can become a tool for malicious activities. This reality affects everyone, from individual consumers to large corporations.
Understanding how this exploitation happens is crucial. Here are some key points to consider:
- Criminals often collect information from various sources.
- Unauthorized access to accounts can lead to huge financial losses.
- Stolen identities can be used for fraudulent activities.
- Online platforms are frequently targeted for personal information.
When personal details are compromised, the repercussions can extend far beyond immediate theft. Phishing attacks, for instance, often rely on harvested information to create convincing scams. Attackers don’t just steal; they manipulate, deceive, and tarnish reputations. Even small pieces of information can enable sophisticated schemes that wreak havoc on one’s life. This connection highlights the immense risk associated with careless handling of sensitive material in the digital age, and it serves as a reminder of the importance of vigilance.
A key aspect that fuels these illegal activities is the sheer volume of available intelligence. Individuals regularly share their lives online, sometimes without realizing the potential consequences. Details such as location, https://medium.com/@hago1994/spokeo-opt-out-step-by-step-guide-155e764ece95 spending habits, and personal preferences provide a goldmine for those with malicious intent. The more comprehensive the profile created, the easier it becomes for criminals to exploit vulnerabilities.
Ultimately, the role of personal information in the realm of illegitimate activities underscores the need for greater awareness and proactive measures. It’s essential for individuals to understand the significance of their online presence and the potential dangers lurking within it. Safeguarding personal details should be a priority, as it’s the first line of defense against unauthorized exploitation.
How Data Brokers Operate

The intricacies of the information marketplace reveal a complex web of operations. Companies acquire vast quantities of personal details from various sources. This can range from social media profiles to public records, creating a treasure trove of insights about individuals. Once consolidated, this information is packaged and sold to clients. These clients can include marketers, financial institutions, and even law enforcement agencies.
While some may see this as harmless, the implications are profound. The transaction of personal insights often bypasses individual consent. Numerous entities engage in this practice, each with different goals and interests. Their methods can significantly affect privacy and security. In many cases, individuals are unaware of the extent to which their lives are scrutinized.
To understand the operation of these entities, it’s essential to examine their methodologies. They often employ advanced algorithms to analyze patterns in collected information. This allows them to create detailed profiles that can predict behavior, preferences, and even vulnerabilities. With information drawn from numerous platforms, they can paint a comprehensive picture of any given individual. This is not merely a business; it becomes a sophisticated game of data aggregation.
| Method | Description |
|---|---|
| Information Gathering | Collecting data from various sources, including websites and public records. |
| Data Analysis | Utilizing algorithms to identify patterns and trends within the data. |
| Profile Creation | Developing detailed profiles for individuals based on gathered insights. |
| Market Selling | Selling aggregated profiles to various clients for targeted strategies. |
In conclusion, the operations conducted by these entities represent a significant challenge to personal privacy. As they continue to refine their techniques, individuals must remain ever-vigilant. Awareness of how personal details are harvested and utilized can empower people to take proactive measures. The landscape of personal confidentiality is shifting rapidly, and understanding these processes is essential for navigating this evolving terrain.
Consequences of Data Misuse
The improper handling and exposure of personal details can lead to significant repercussions. Individuals may experience financial loss, emotional distress, and a breach of privacy. These outcomes ripple through various aspects of life. Understanding the scope of these consequences is essential for effective self-defense against potential threats. Without taking the necessary precautions, anyone can find themselves vulnerable to this growing issue.
One prevalent consequence is identity theft. Criminals use stolen identities to commit fraud, often leading to severe financial difficulties for their victims. The emotional toll can be equally devastating, resulting in anxiety, depression, and a sense of violation. Many individuals find it challenging to fully regain their trust in privacy once it has been compromised.
Furthermore, victims often face the daunting task of restoring their reputations. Once personal information is out there, it can become nearly impossible to reclaim control. This ongoing struggle requires time, resources, and emotional resilience. Not everyone has the means to navigate this complex process effectively.
Beyond personal distress, there are serious implications for businesses as well. Companies can suffer reputational damage if they are found to mishandle sensitive information. Loss of customer trust often translates into decreased sales and lingering skepticism. Ultimately, organizations must prioritize robust security measures to safeguard against potential breaches.
As regulations evolve, the legal consequences of mismanaged details are becoming more stringent. Organizations that fail to comply with privacy laws may face hefty fines and penalties, which can significantly impact their financial health. In an era where consumers are more aware of their rights, the long-term effects of negligence can be catastrophic.
In light of these challenges, taking proactive steps is vital. Awareness of potential risks enables individuals to protect themselves more effectively. Tools such as identity monitoring services can provide an additional layer of security. Regularly updating passwords and being cautious with sharing personal information can also help minimize exposure.
Ultimately, the consequences of mishandled details extend far beyond immediate financial loss. Emotional wellness, public perception, and legal standing all hang in the balance. Navigating the complex landscape of privacy requires vigilance and a commitment to ongoing education. Those who take these steps not only protect themselves but contribute to a more secure digital environment for everyone.
Protecting Yourself from Data Theft
In today’s interconnected world, keeping your personal details secure has become increasingly challenging. With numerous platforms collecting and sharing private information, it’s essential to understand how to safeguard your identity. A proactive approach can drastically reduce the risk of exposure. Awareness is the first step in preventing unauthorized access. Many individuals underestimate the potential dangers lurking online.
Selecting strong passwords for all accounts is crucial. Use a combination of letters, numbers, and symbols to enhance security. Regularly updating passwords can also assist in keeping intruders at bay. Moreover, enabling two-factor authentication adds another layer of protection, making unauthorized access even more difficult. Consider this: those small, seemingly insignificant details you share can lead to significant consequences.
Be cautious about where and how you share your information. Social media platforms, for instance, can be a double-edged sword. While they allow for connections, they also expose users to potential threats. Always think before you post. Ensure your privacy settings are properly adjusted to limit visibility to a select circle.
Utilizing reputable antivirus software is another effective strategy. These programs can detect and eliminate potential threats, providing peace of mind. Regular system scans are essential for identifying vulnerabilities that might otherwise go unnoticed. Furthermore, consider using a virtual private network (VPN) to encrypt your internet connection and shield your online activities from prying eyes.
Education plays a vital role in protection. Stay informed about the latest security practices and common online scams. Recognizing potential threats is half the battle in securing your assets. Remember that cybercriminals continuously evolve their tactics, so staying one step ahead is imperative for maintaining your security. In an ever-changing digital landscape, vigilance is the key to enduring safety.
Trends in Cybercrime Tactics
As technology evolves, so do the tactics utilized by malicious actors in the digital landscape. This constant change can be perplexing and alarming. New strategies emerge, reflecting the ever-shifting reality of online threats. The target can be anyone, from individuals to large corporations. Understanding these trends is crucial for anyone who operates in today’s interconnected world.
One notable trend is the rise of ransomware attacks. These incidents have surged in recent years. Cybercriminals encrypt files on a victim’s system and demand payment in exchange for the decryption key. The prevalence of these attacks has prompted widespread concern. Victims often face tough choices–pay the ransom or lose their data forever.
Moreover, phishing schemes have become more sophisticated. Attackers now craft emails that mimic trusted sources. This makes it increasingly difficult for unsuspecting individuals to identify scams. As a result, many people fall prey to these deceptive tactics. Phishing remains a preferred method due to its effectiveness in harvesting sensitive details.
Additionally, social engineering techniques are evolving, targeting human psychology. Scammers exploit emotions such as fear or urgency. They create scenarios that press individuals into making quick decisions. This manipulation often leads to severe consequences for the victim. Increasing awareness about these psychological tactics can be a game changer.
- Emerging technologies are also being leveraged by cybercriminals.
- Artificial intelligence and machine learning enhance their capabilities.
- These tools allow rapid analysis of vulnerabilities.
- Automated attacks can occur at unprecedented speeds.
The integration of these technologies allows for greater efficiency in executing attacks and makes it harder for security systems to keep up. Continuous adaptation and learning from past experiences empower those with malicious intent to refine their strategies.
In addition, the surge in remote work has opened new avenues for potential intrusions. With more people accessing sensitive systems from home, attackers can exploit unsecured networks. This shift in working practices presents unique challenges for cybersecurity. Companies must be vigilant in maintaining robust defenses.
Finally, a concerning trend is the emergence of underground markets. These online spaces facilitate the buying and selling of stolen information and hacking tools. The accessibility of such resources lowers the bar for entry into cybercrime. As a result, even novice hackers can perpetrate significant damage.
Understanding these evolving tactics is essential for bolstering defenses. Awareness is the first line of defense in this ongoing battle against cyber threats. By staying informed, individuals and organizations can adopt proactive measures to safeguard themselves against ever-evolving risks.
Trends in Cybercrime Tactics
The landscape of online criminal activities is continuously evolving. As technology advances, so do the methods employed by malicious actors. Understanding these shifts is vital for both individuals and organizations. New tactics appear frequently, presenting fresh challenges for cybersecurity.
One notable trend is the increasing sophistication of phishing schemes. These attacks are no longer simple email scams; they have become highly targeted and personalized. Cybercriminals utilize social engineering techniques to build trust. Their goal is to deceive individuals into revealing sensitive information.
- Ransomware attacks are on the rise, affecting both businesses and individuals.
- Malicious software can encrypt files, demanding payment for restoration.
- The use of cryptocurrencies makes tracing transactions difficult.
- Supply chain attacks have gained traction, affecting numerous organizations at once.
Another alarming trend is the targeting of remote workers. With the shift to remote operations, vulnerabilities have emerged in home networks. Cybercriminals exploit these weaknesses to gain unauthorized access. They aim to infiltrate corporate systems through less secure home devices. The shift to remote work has created a rich hunting ground for attackers, who now focus on exploiting the less fortified digital environments of individual users.
- Artificial intelligence is being weaponized to enhance cyber attacks.
- Automated bots can now launch attacks at an unprecedented scale.
- Adversaries are increasingly using machine learning to optimize their strategies.
Social media platforms also present new opportunities for exploitation. Scammers employ fake accounts to impersonate trusted figures. They often use these accounts to spread misinformation or solicit personal data. The viral nature of social networks amplifies these threats, making it easier for malicious campaigns to gain traction. This strategy allows criminals to tap into existing networks of trust, creating a façade that can easily deceive unsuspecting users.
Moreover, the rise of IoT devices has introduced additional vulnerabilities. Each connected device can be an entry point for attackers. As households become smarter, the average user often neglects security measures. This oversight creates a plethora of opportunities for exploitation. Cybercriminals are quick to recognize and act upon these weaknesses, often leading to significant breaches.
In conclusion, as tactics employed by online criminals continue to adapt, awareness and vigilance become essential. Keeping abreast of these trends is necessary for effective defense strategies. Organizations must prioritize cybersecurity training, while individuals should adopt proactive measures to protect their digital lives. The fast-paced evolution of techniques means that staying informed is not merely beneficial–it is crucial in the ongoing battle against digital threats.
Future of Data Privacy Regulations
As society continues to evolve in the digital age, the conversation surrounding the safeguarding of personal details becomes increasingly pertinent. Authorities and organizations are recognizing the need for robust frameworks to protect individuals. The current landscape is dynamic and ever-changing. Technological advancements push the boundaries of existing regulations. New challenges emerge regularly, demanding innovative solutions.
The landscape of privacy laws is constantly shifting. With the rise of emerging threats and the exploitation of personal details, lawmakers are under pressure to adapt. This adaptation will likely involve more stringent requirements for transparency and consent. Individuals are becoming more aware of their rights, and they seek enhanced protection. They desire accountability from those who handle their sensitive data. This evolving awareness could lead to more collaborative approaches between authorities and citizens.
Global standards will play a crucial role in shaping future regulations. Different regions are taking varied approaches to the issue. For example, while some countries are implementing strict guidelines, others remain lenient. The interplay between local and international laws will create challenges and opportunities. Countries may need to harmonize their regulations to ensure consistency in enforcement and compliance. This harmonization could pave the way for cross-border collaborations, ultimately leading to stronger defenses against the misuse of personal details.
Moreover, technological innovations will significantly influence the regulatory framework. Advancements such as artificial intelligence and blockchain are already changing how information is secured and shared. These technologies can enhance compliance measures and facilitate better monitoring of regulatory adherence. However, they also pose new questions regarding ethics and governance. Striking a balance between innovation and protection will be paramount.
In addition, public sentiment will shape future policies. As individuals become more vocal about their privacy concerns, lawmakers must respond. Public protests and advocacy campaigns could lead to the enactment of stronger safeguards. This engagement from citizens can catalyze meaningful change. Importantly, a collaborative approach involving tech companies, regulators, and consumers may hold the key to effective privacy legislation.
Ultimately, the future of privacy regulations will hinge on adaptability, collaboration, and a proactive stance against emerging threats. As we embrace new technologies and methodologies, the emphasis on protecting personal information will become more critical than ever. It is essential for all stakeholders to remain vigilant, ensuring that the rights of individuals are upheld in an increasingly complex digital realm. The journey towards a secure and transparent environment continues, driven by the collective understanding of what it means to safeguard our most valuable asset: our privacy.
